
“Kaseya Attack”: Over 1000 organizations globally attacked on Fourth of July weekend, biggest supply chain attack since Sunburst
Highlights
- Massive supply chain attack carried out by REvil over the 4th of July weekend impacts numerous Kaseya customers with millions of USD in ransom demands
- Check Point Research (CPR) observes 15 new REvil attacks per week in the past 2 months with US, Germany, Brazil and India being the top countries affected by such attacks
- Ransomware attacks continue to surge globally, hitting a 93% increase year on year
- Attacked Check Point Harmony Endpoint customers remain protected
Anyone hoping for a quiet 2021 after experiencing a year of the COVID-19 pandemic had no idea what was coming their way. It looks like the year is turning out to be a year of attacks. There was the Sunburst attack, believed to be one of the most sophisticated and severe attacks ever seen in the wild, followed by the “Hafnium” (aka Microsoft Exchange server) attack, and the Colonial Pipeline attack as well as a global surge in ransomware incidents. All these meant that security professionals hardly had a single day of respite. Unfortunately, over the weekend of July 4th, another attack struck yet again.
What Happened?
IT management software company Kaseya, a cloud-based managed security services provider (MSSP) platform that allows MSSPs to perform patch management and client monitoring for their customers, experienced a massive attack over the weekend, affecting numerous organizations by what appears to be a global supply chain attack. Kaseya issued a security advisory on their site, warning all customers to immediately shut down their VSA server to prevent the spread of the attack while they investigated. At least 1,000 businesses are said to have been affected by the attack, with victims identified in at least 17 countries.
It would appear that the timing of the attack was no accident and that the Russian speaking ransomware gang REvil, aka Sodinokibi, deliberately chose the 4th of July weekend to strike.
To breach on-premise Kaseya VSA servers, REvil used a zero-day vulnerability that was in the process of being fixed. The vulnerability had been previously disclosed to Kaseya by security researchers from the Dutch Institute for Vulnerability Disclosure, and Kaseya was validating the patch before rolling it out to customers. However, the REvil ransomware gang was one step ahead of Kaseya and used the vulnerability to carry out their attack. The ransom demand ranged from US$45K to US$5 million.
With the attack on Kaseya VSA servers, REvil’s affiliate was initially targeting Kaseya’s MSSP’s, with a clear intent to propagate to the MSSP customers. The attack amplified exponentially and profitably from the MSSP to the actual customers.
Threat Actors that deploy ransomware continue to take advantage of national holidays in various countries. During a holiday period or over a weekend, companies often operate with a skeleton crew with fewer staff to keep an eye out for incidents. This helps the threat actors in several ways:
- It allows the ransomware to be fully deployed before anyone notices.
- It induces more panic during response operations especially if key players within the victim’s environment are unavailable to respond. This in turn could increase the chances that a ransom demand being paid.
The Forensics of the Attack
The actual attack started by utilizing existing operating system files like PowerShell, and CertUtil. However, the truly unusual part of this attack involves the use of an old version of Microsoft’s own antivirus for encryption. This allowed the encryption to be hidden from most security products that ignore Microsoft’s AV.
Kaseya VSA is cloud-based and allows MSSPs to perform patch management and client monitoring for their customers. Attackers used this fact to drop in a file that was distributed to this set of customers, while disabling various Microsoft Defender security mechanisms, so that the malicious file could launch its encryption process.
Check Point Harmony Endpoint’s Forensics Report of the REvil Kaseya Attack
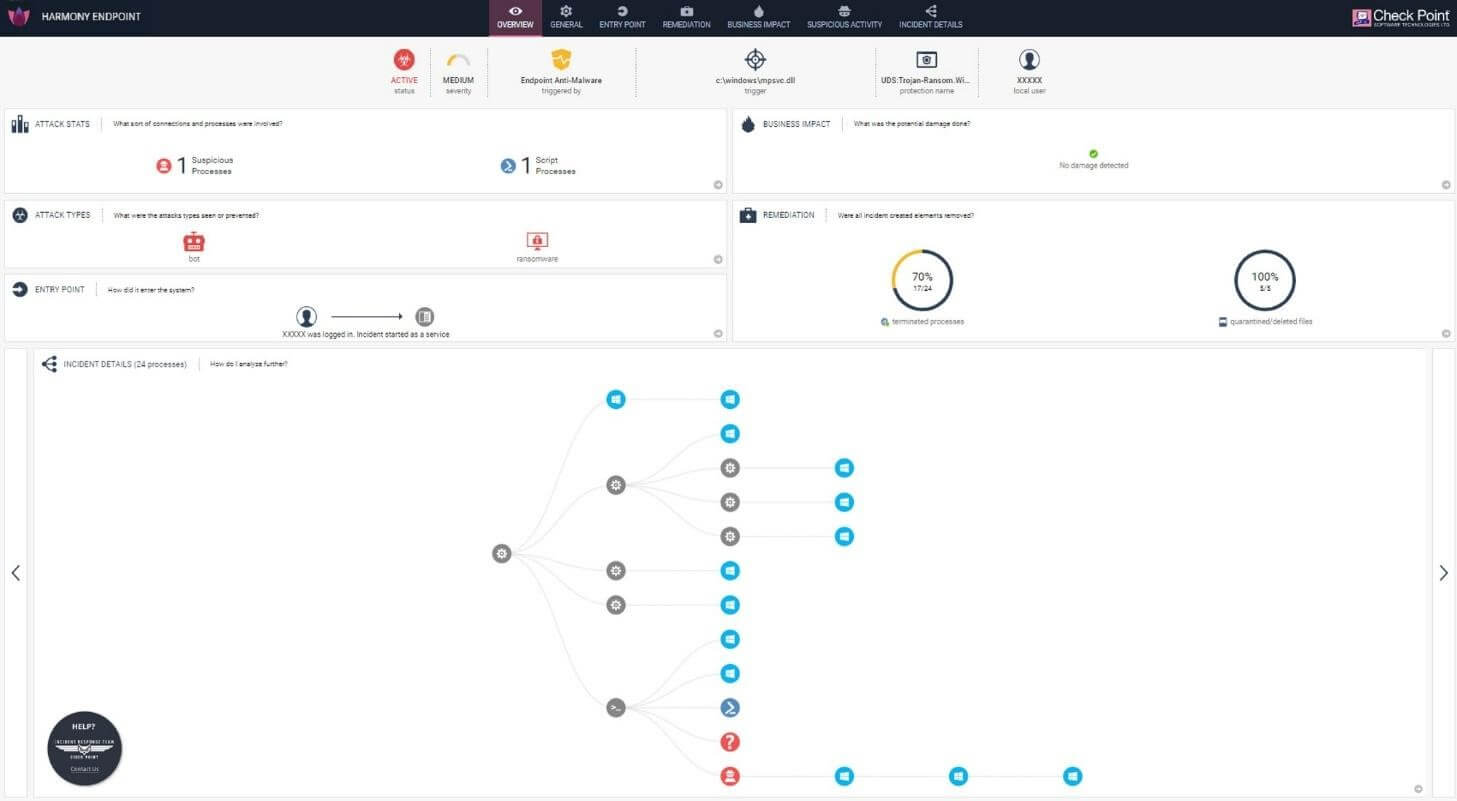
Check Point Harmony Endpoint – Check Point’s complete Endpoint Protection Platform (EPP) & Endpoint Detection & Response (EDR) solution was able to promptly detect and prevent the attack at multiple levels for all customers that were targeted. The solution’s forensics report (now publicly available) provides an in-depth overview of the attack chain and remediation.
About REvil Group
REvil is one of the most prominent ransomware families globally. Operated by the Russian-speaking REvil group, the ransomware family is responsible for dozens of major breaches since 2019. In the last 2 months CPR observed 15 new REvil attacks weekly.
One of the key factors driving REvil’s success is their use of the Double Extortion technique, where threat actors steal data from organizations in addition to encrypting the files. This means that, as well as demanding a ransom to decrypt data, attackers can later threaten to leak the stolen information, if an additional payment is not made.
REvil is also known for their collaboration with affiliate hackers, joining forces with advanced attackers, who are responsible for breaching new targets, exfiltrating data, and encrypting networks. In turn, the REvil group provides these affiliates with the ransomware itself, the leak site and even share profits with them.
On a wider scale, the REvil ransomware group announced in February 2021 that they have added two stages to their Double Extortion scheme: DDoS attacks and phone calls to the victim’s business partners and media. The group now offers DDoS attacks and voice-scrambled VOIP calls to journalists and colleagues as a free service for its affiliates, to apply further pressure on the victim company to meet ransom demands within the designated timeframe.
In April 2021, REvil demonstrated the use of what we call a Triple Extortion technique. Here, the gang successfully breached Quanta Computer, a prominent Taiwan-based notebook original design manufacturer (ODM) and a prominent business partner of Apple. Following the ransomware attack, a payment of some US$50 million was demanded, along with a warning that the sum would be doubled unless it was paid on time. Since the company refused to communicate with the threat actors, the threat actors went on to extort Apple directly, demanding that Apple purchase back blueprints of their products found on Quanta Computer’s network. Approximately a week later, REvil peculiarly removed Apple’s drawings from their official data leak website.
Closing note: Following DarkSide’s ransomware attack on the Colonial Pipeline and the subsequent pressure from international law enforcement, major underground Russian communities banned the future promotion of ransomware affiliate projects such as REvil. We are still waiting to see how this will unfold and affect ransomware operations such as REvil in the future.
Check Point Harmony Endpoint – securing today’s remote workforce
Check Point Harmony Endpoint is a complete endpoint security solution built to protect the remote workforce from today’s complex threat landscape. It prevents the most imminent threats to the endpoint such as ransomware, phishing, or drive-by malware, while quickly minimizing breach impact with autonomous detection and response. The solution’s forensics is a patented set of algorithms designed to build the end-to-end attack flow (the “attack story”) clearly and accurately. The forensics view provides an accurate process tree of the attack, detailed view of the entry point, detailed description of the business impact and allocates the files deleted/encrypted, with remediation process details – what was automatically remediated and what are the attack residuals.
Check Point Harmony Endpoint is part of the Check Point Harmony product suite, the industry’s first unified security solution for users, devices and access. Check Point Harmony consolidates six products to provide uncompromised security and simplicity for everyone. Discover its capabilities by yourself, and schedule a personalized demo to see it in action.
What is a Software supply chain attack?
In a software supply chain attack, the threat actor typically installs malicious code into legitimate software by modifying and infecting one of the building blocks the software relies upon. As with physical chains, software supply chains are only as strong as their weakest link.
Software supply chain attacks can be divided into two main categories. The first includes targeted attacks aiming to compromise well-defined targets, scanning their suppliers list in search of the weakest link through which they could enter. In the second category, software supply chains are used to compromise as many victims as possible by locating a weak link with a large distribution radius.
Avoid becoming the next victim of ransomware
Kaseya has issued several recommendations to their affected clients following the attack, including advice to shut down and remain offline until further notice. Enclosed are a few extra security “hygiene” recommendations to remain protected from the next attack:
- Be extra vigilant on weekends and holidays.Most ransomware attacks over the past year have taken place on weekends or over holidays, when organizations are more likely to be slower to respond to a threat.
- Install updates and patches regularly.WannaCry hit organizations around the world hard in May 2017, infecting over 200,000 computers in three days. Yet a patch for the exploited EternalBlue vulnerability had been available for a month before the attack. Updates and patches need to be installed immediately and have an automatic setting.
- Install anti-ransomware. Anti-ransomware protection watches for any unusual activity such as opening and encrypting large numbers of files, and if any suspicious behavior is detected, it can react immediately and prevent massive damage.
- Education is an essential part of protection.Many cyberattacks start with a targeted email that does not contain malware, but uses social engineering to try to lure the user into clicking on a dangerous link. User education is therefore one of the most important parts of protection.
- Ransomware attacks do not start with ransomware, so beware of other malicious codes,such as Trickbot or Dridex that infiltrate organizations and set the stage for a subsequent ransomware attack.
- Backing up and archiving data is essential.If something goes wrong, your data should be easily and quickly recoverable. It is imperative to back up consistently, including automatically on employee devices, and not rely on them to remember to turn on the backup themselves.
- Limit access to only necessary information and segment access.If you want to minimize the impact of a potentially successful attack, then it is important to ensure that users only have access to the information and resources they absolutely need to do their jobs. Segmentation minimizes the risk of ransomware spreading uncontrollably across the network. Dealing with the aftermath of a ransomware attack on one system can be difficult, but repairing the damage after a network-wide attack is much more challenging.
The Check Point Incident Response Team (IRT) is available 24x7x365 to deliver security incident handling. Organizations that believe they have been exposed to this attack can call Check Point’s IRT hotline. Check Point’s security experts will help you contain the threat, minimize its impact, and keep your business running.









