If you are using a VPN service or planning to get one, there are certain features you need to understand to make the most of it. Some of these features are just marketing gimmicks and VPN providers often rename them to make them sound more sellable. But there are other features that form the core of a VPN, and it’s important to ensure that they function well.
Most VPN services come with important features activated by default, so you won’t need to touch and set them up yourself. However, there are a handful of features that you can tweak to make them more useful for your specific use case.
So, what are these VPN features, and how do they work?
1. Encryption
One of the main functions of a VPN is to block attempts by unauthorized users to intercept, read, or alter the content of your internet traffic. It achieves this by converting your actual data into an unreadable and coded format through a process called encryption.
The data is protected using an encryption key set only by authorized users. To decrypt the data, you’ll need a similar decryption key.
A VPN encrypts your data when it enters through its tunnel and then turns it back into the original format at the other end.
There are three types of encryption techniques that most VPNs use. These are:
i. Symmetric Encryption
Symmetric encryption is an ancient form of cipher that uses an algorithm to transform data. The “key” is a factor in the algorithm that changes the entire outcome of the encryption. Both the sender and receiver use the same key to encrypt or decrypt data.
These algorithms group data into a series of grids and then shift, swap, and scramble the content of the grids using the key. This technique is called block cipher and forms the basis of frequently used key encryption systems including AES and Blowfish.
- AES:
The Advanced Encryption System or AES is a block cipher commissioned by the US government and used by most VPN services worldwide. It breaks up streams of data into a 128-bit array, which equals 16 bytes.
The key can either be 128, 192, or 256 bits in length while the blocks are grids of 4x4 bytes. If you aren’t familiar with data units, you should learn to distinguish the bits and the bytes.
The length of the key determines the number of encryption rounds or the passes of transformation. For instance, the AES-256 performs 14 rounds of encryption, making it extremely secure.
- Blowfish:
Users who distrust the security offered by AES use Blowfish. It uses an open-source algorithm which is why it’s also included in the open-source OpenVPN system.
However, on a technical level, Blowfish is weaker than AES since it uses a 64-bit block—half the size of the AES grid. This is why most VPN services prefer AES over Blowfish.
ii. Public Key Encryption
An obvious flaw with the symmetric encryption system is that both the sender and receiver need to have the same key. You’ll have to send the key to the VPN server to start communication. If interceptors somehow acquire the key, they can decrypt all the data encrypted with it. Public Key Encryption offers a solution to the security risk in key transmission.
Public Key Encryption systems use two keys, one of which is made public. Data encrypted with the public key can only be decrypted with the corresponding decryption key and vice versa.
iii. Hashing
Hashing is the third encryption method used by VPNs. It uses a Secure Hash Algorithm (SHA) to preserve the integrity of data and confirm that it came from the original source.
SHA is part of the OpenSSL library used by most VPNs. In hashing algorithms, the hashing process is used to retrieve the certificate and confirm that the certificate data has been sent by the certifying authority rather than some interceptor.
2. Split Tunneling
Split tunneling is a popular VPN feature that lets you choose which apps to secure with the VPN and which apps can work normally. It’s a useful feature that helps you keep some of your internet traffic private and routes the rest through the local network.
Split tunneling can be a useful tool to save some bandwidth as it only sends a portion of your internet traffic through the tunnel. So, if you have sensitive data to transfer, you can protect it without experiencing the inevitable lag in other online activities caused by the VPN.
3. Data and Bandwidth Caps
Data and bandwidth caps are limits that determine the amount of data you can transfer or the bandwidth you can use at a time. VPN services use data and bandwidth limits to control the amount and rate of flow of data across the network.
It’s important for VPN service providers to keep limits in order to prevent network congestion and outages. However, premium service providers with extensive infrastructures like ExpressVPN, NordVPN, PIA, and Surfshark don’t put any data and bandwidth limits on usage.
4. No-Logs Policy
The no-logs or zero-logs policy is a VPN’s promise to never keep a record of the online activities of a user. No-logs policy is a major selling point for VPNs as it’s one of the main reasons why people use VPNs in the first place.
Not many VPNs offer a complete zero-logs service and even those with strict no-logs claims tend to store some logs. If you aren’t sure which VPN to choose for a truly no-logs service, look for those that use RAM-only servers. Such servers save temporary data which is erased as the hardware is turned off.
5. Simultaneous Device Connections
Simultaneous device connections refer to the number of devices that can connect to a VPN at the same time. Most VPNs place a limit on simultaneous connections and only a handful of them can accommodate unlimited connections at a time.
One thing to remember with multiple device connections is that you can install the VPN on as many devices as you like, but you can’t have them running on all the devices at once.
6. Kill Switch
A VPN kill switch is a feature that disconnects your device from the internet if your VPN connection drops unexpectedly. It’s a vital VPN feature that prevents you from sending data outside the secure VPN tunnel.
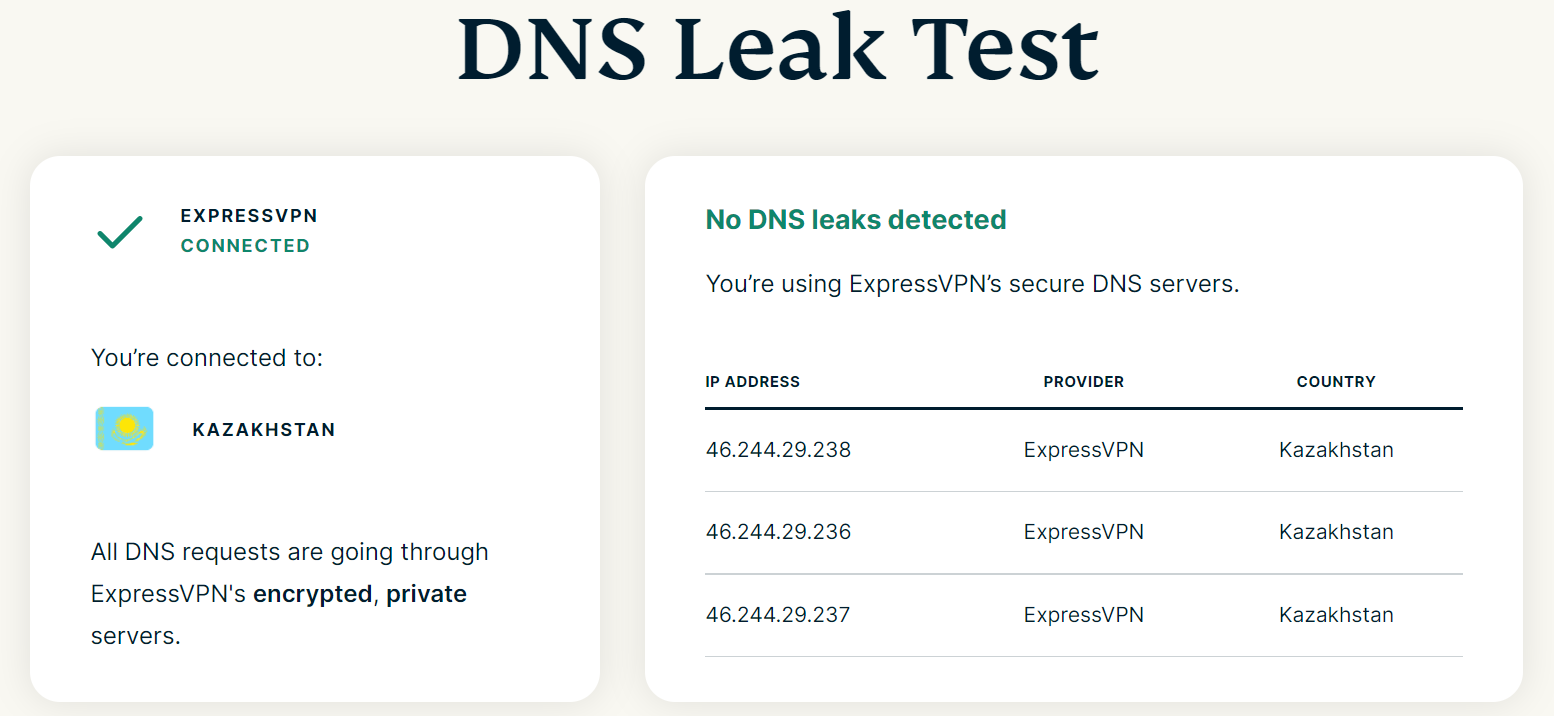
7. Leak Protection
The main purpose of using a VPN is to hide your actual IP address from prying eyes. But sometimes your original IP address may get revealed, exposing your location, browsing history, and internet activity online. Such an incident is referred to as an IP leak or VPN leak, and it beats the purpose of using a VPN.
Many top VPNs have built-in IP/DNS leak protection that is enabled by default. They also offer tools to check your actual IP and the address assigned to you by the VPN. With an active VPN connection, the two IP addresses should not match.
8. IP Shuffle
IP shuffling is a VPN privacy feature that randomizes your IP address. A VPN does so by reconnecting you to a different VPN server after a given interval. Most VPNs allow users to set up the shuffling frequency anywhere from every 10 minutes to once an hour or a day.
Get Premium Anonymity With a VPN
With rising security threats, VPNs have become indispensable tools to achieve protection. When choosing a VPN, your top priority should be a service with a strict no-logs policy and security features like a VPN kill switch and leak protection.
By understanding the VPN lingo and how the various features work, you will be able to choose a VPN service that fits your needs.